

Top-tier security and privacy
with robust defenses, secure development practices, and strict data protection measures
Keeping your information safe at every level
Our platform follows a comprehensive Secure Development Life Cycle (SDLC) to ensure software security from the start, incorporating secure coding principles and thorough security testing. We maintain the highest level of information security through strict access controls, encryption, and continuous monitoring, in line with industry standards like ISO 27001.
Product Security
We implement a wide range of defenses to protect against cyber threats. We employ robust network security measures, including firewalls, intrusion detection, and secure network configurations, to shield against unauthorized access and malicious activity. Our threat detection systems continuously monitor for potential risks, using real-time intelligence to prevent malware, ransomware, and other cyber attacks before they can cause harm.
In addition, we maintain a comprehensive incident response plan to swiftly address any cyber threats. Regular security patches and updates ensure our systems are protected against newly discovered vulnerabilities, while data backups and disaster recovery plans safeguard your information in the event of an attack. Our platform also includes phishing prevention measures, educating users and employees on recognizing and avoiding social engineering attacks.
Information Security
We are committed to ensuring the highest level of information security, adhering to industry standards such as ISO 27001. We implement strict access controls, encryption, and continuous monitoring to protect the confidentiality, integrity, and availability of your data. Our security protocols encompass secure access, both at rest and in transit, ensuring that only authorized users can interact with sensitive information. We also follow a comprehensive incident response plan to quickly detect, mitigate, and recover from any security incidents.
Additionally, we regularly conduct vulnerability assessments, security testing, and maintain audit logs to proactively identify and address potential risks. Our platform meets stringent regulatory and compliance requirements, safeguarding your data in line with best practices and industry regulations. We also ensure that our cloud infrastructure providers comply with our high security standards, so your information remains protected at all levels of our infrastructure.
Cybersecurity
Our platform adheres to a rigorous Secure Development Life Cycle (SDLC) to ensure the security and integrity of our software and systems. We have established clear rules for secure development practices, and our teams consistently apply secure coding principles throughout the development process. This approach minimizes vulnerabilities from the start, creating a robust foundation for our software.
Additionally, security testing is a critical part of our development life cycle, ensuring that all systems undergo thorough testing before release. Test data is carefully selected, protected, and managed, guaranteeing that sensitive information remains secure during the testing phases.
Privacy
We ensure that all data and associated assets are handled and protected according to documented rules and procedures, including the classification of information based on its confidentiality, integrity, and availability. All data is labeled and managed according to strict security guidelines, ensuring it is safeguarded from loss, destruction, unauthorized access, or release. Additionally, records are securely deleted when no longer needed, and data masking is implemented to protect sensitive information in line with regulatory requirements and our internal policies.
We also enforce robust data leakage prevention measures across our systems, networks, and devices to ensure the security of sensitive data at all times. By adhering to industry best practices and relevant legislation, we ensure that your information is handled with the utmost care, supporting both your privacy and our organizational requirements for information security.
SOC 2 Compliance
Lupa Technology has completed the AICPA SOC 2 Type 1 audit for Security, affirming our commitment to protecting client data with robust, well-designed internal controls.
This independent attestation, performed by Accedere, confirms that our systems were properly designed to meet the Trust Services Criteria for Security. It assures partners and clients that we uphold strong safeguards across our cloud-based platform and operations.
Our SOC 2 compliance reflects our dedication to operational excellence, risk mitigation, and continuous improvement. We maintain strict access controls, enforce secure system configurations, and monitor infrastructure performance and threats in real time.
This disciplined approach helps ensure security of the data entrusted to us, especially by clients working in high-stakes, data-intensive industries like construction and legal.
Latest Resources from LUPA
Whether you’re looking to dig deeper into our technology, find helpful tips, or simply explore fresh ideas, we’ve got something for you.
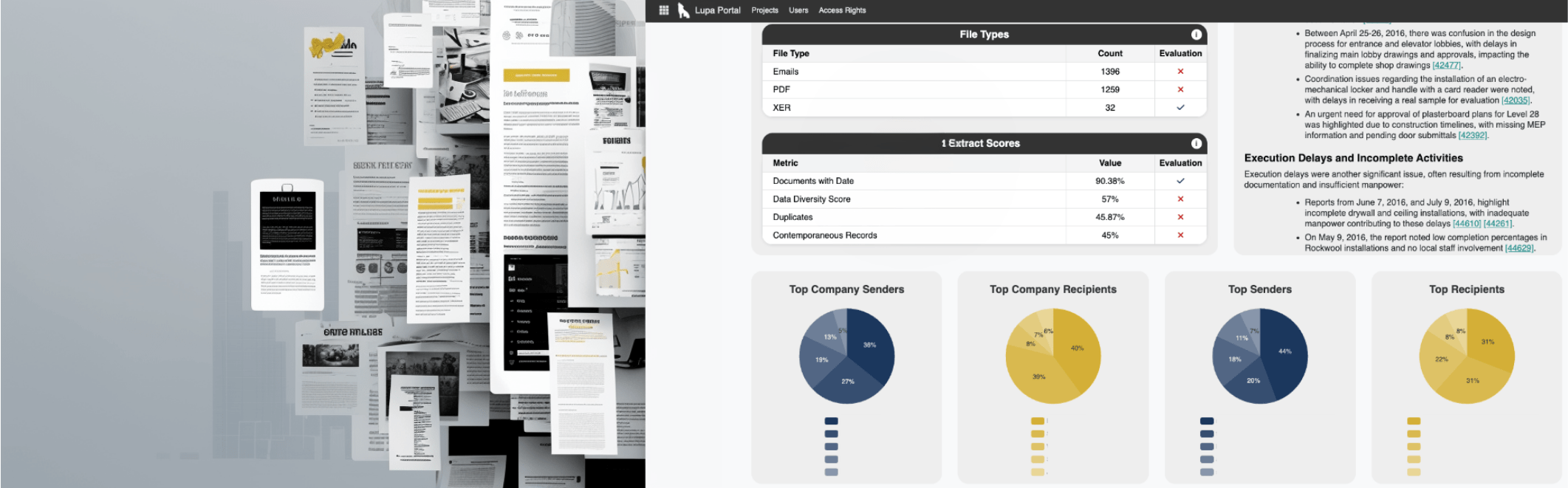
Timeline, solved – an evidence-first chronology for claims & disputes
A dispute is brewing. Leadership asks the simplest question that is never simple: what, exactly, happened, and when? The record lives everywhere – emails, RFIs, minutes, letters, program snapshots. Memories don’t match, the clock is ticking, and the stakes are real.

Stop Chatting with AI, Start Getting Real Answers
It seems like almost every team today is experimenting with AI assistants. Chatbots that summarize text, draft emails, or brainstorm ideas are everywhere. They’re helpful for simple tasks. But here’s the truth nobody talks about.

Construction technologies: Overview of tools and case studies
Click to open and read the full article.




